Reverse Engineering Android Apps Part1 : Apktool
Posted on June 7, 2016 • 3 minutes • 546 words
Table of contents
In this post i want to show you, how to reverse engineer Android apps with Apktool. Disclaimer : This guide is for educational purposes only. Copying/Reusing the decompiled code other than this example might be illegal. Please check the license !
1) Background
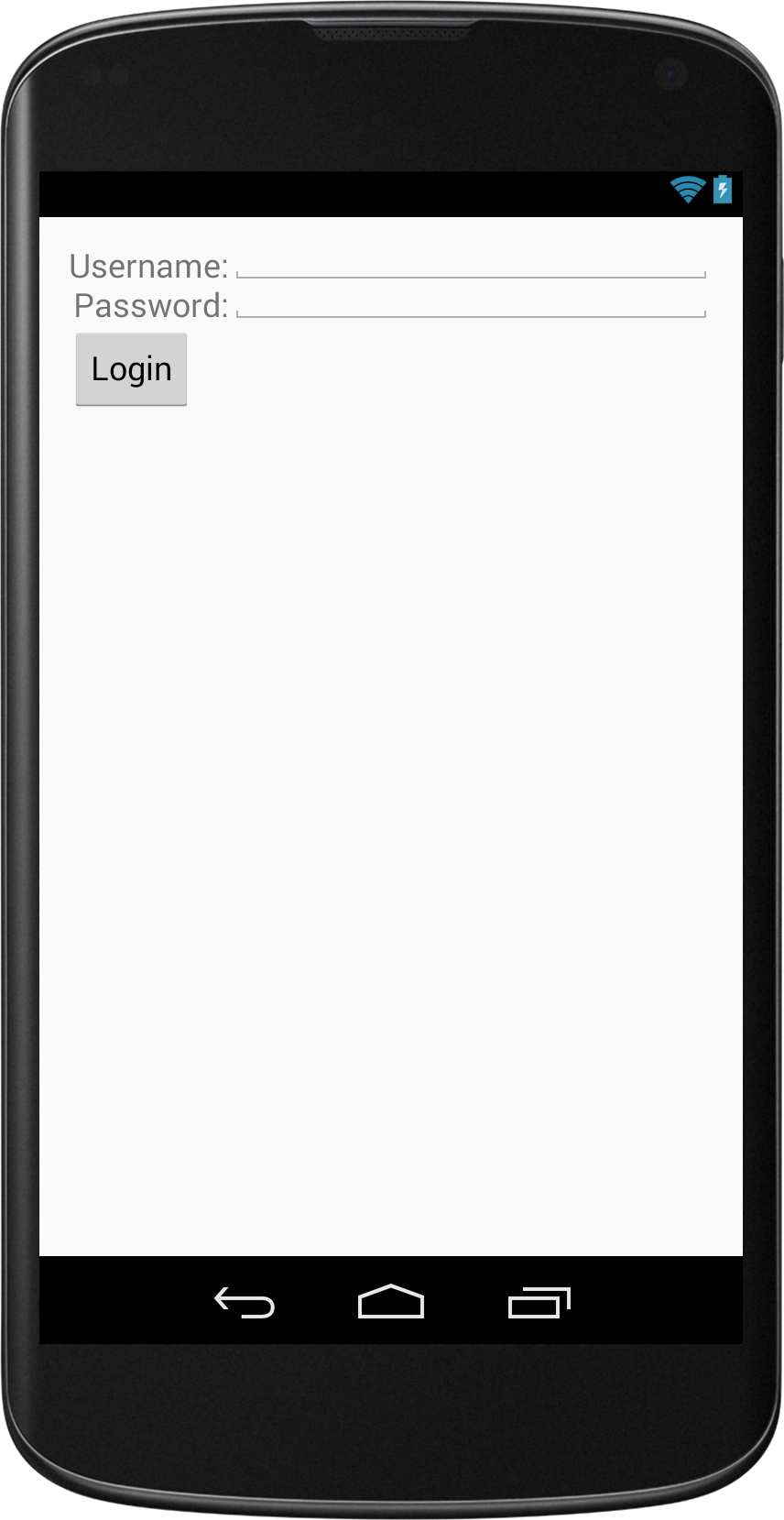
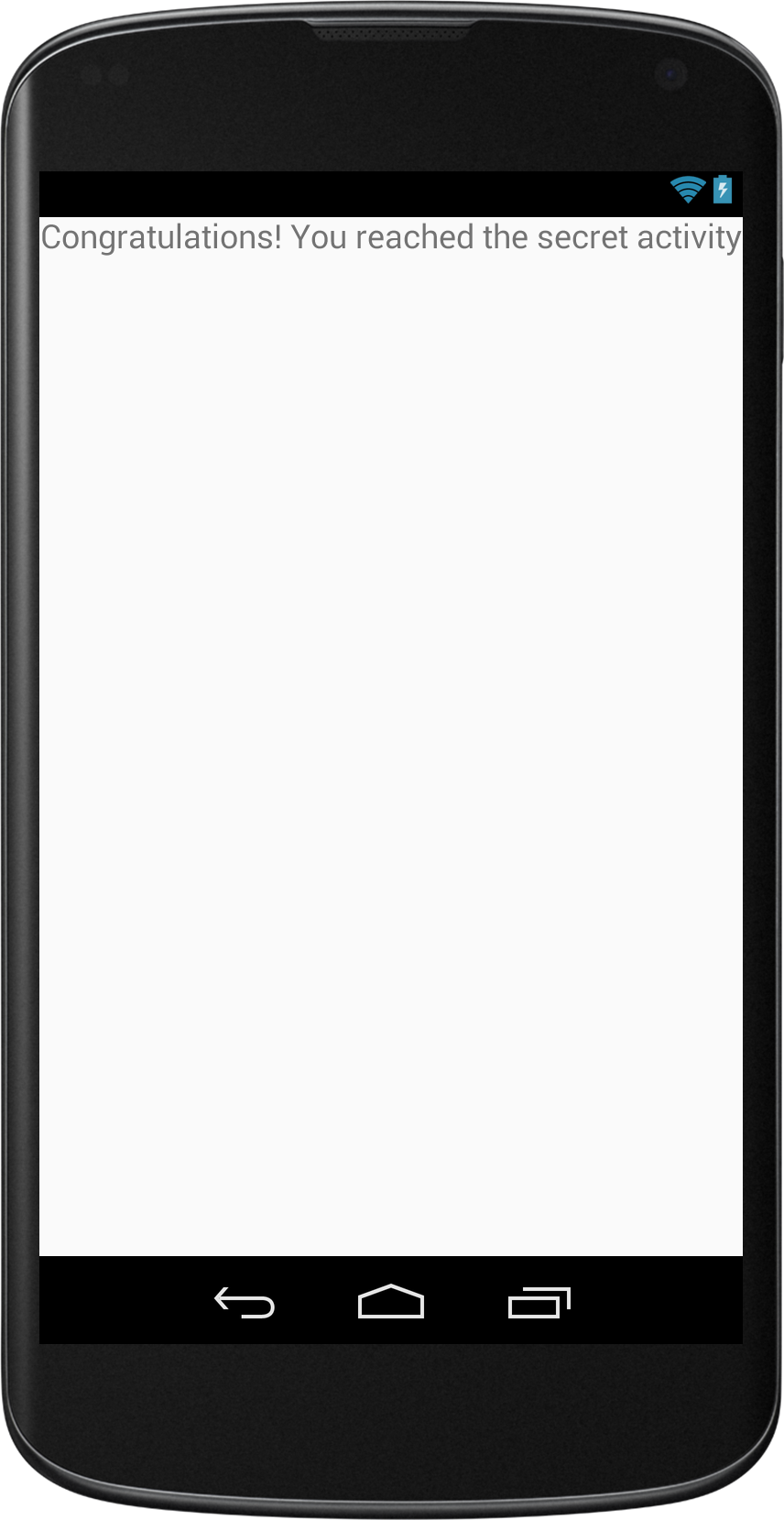
A few days ago i wanted to know how hard it is to change a compiled Android app. I wanted to find out how much is possible and what is the best way to protect apps against it. It turns out that it's not that hard, if you don't use any obfuscation techniques.I created a simple example app. In this example i’m trying to bypass the login check, to get to the “SecretActivity”.
2) Grab the apk over adb
In this example you can just download the apk from my Github Profile, but here's a way to grab apk's from already installed apps.With this command you get a list of all installed packages:
adb shell pm list packages
This command should return the path of the apk:
adb shell pm path jensklingenberg.de.ReverseMev1
This downloads the apk:
adb pull /data/app/jensklingenberg.de.ReverseMev1-1/base.apk
3) What is inside an apk?
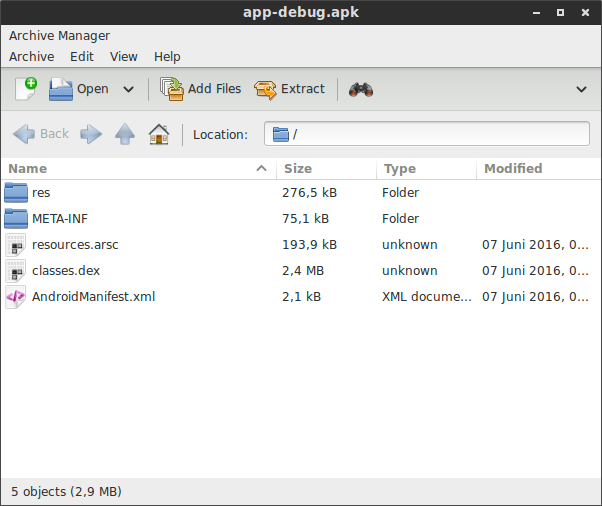
An apk is nothing else than a zip file. You can open it with any archive manager.Usually it contains the AndroidManifest.xml, the ressource folders and a classes.dex, which contains the dalvik bytecode (Dalvik EXecutable)
4) Install Apktool
Follow the instructions on http://ibotpeaches.github.io/Apktool/install/ Apktool converts the dex file to smali bytecode, which is human readable code.Disassemble the app
apktool d ReverseMe.apk
Apktool will generate a new folder with the extracted files from the apk.
Android Manifest
The first file we to take a look at is the android manifest. Here we can see which is the activity that is opened first.As we can see here, the class MainActivity has the intent filter action android.intent.action.MAIN this means that this class is the entry class.
<?xml version="1.0" encoding="utf-8"?>
<manifest xmlns:android="http://schemas.android.com/apk/res/android" package="jensklingenberg.de.ReverseMev1">
<application android:allowBackup="true" android:icon="@mipmap/ic_launcher" android:label="@string/app_name" android:supportsRtl="true" android:theme="@style/AppTheme">
<activity android:name="jensklingenberg.de.ReverseMev1.MainActivity">
<intent-filter>
<action android:name="android.intent.action.MAIN" />
<category android:name="android.intent.category.LAUNCHER" />
</intent-filter>
</activity>
<activity android:name="jensklingenberg.de.ReverseMev1.SecretActivity"></activity>
</application>
</manifest>
5) Change the bytecode
We can find the MainActivity in the smali folder.This was the method checkLogin() in MainActivity.java :
public boolean checkLogin(String username,String password){
//Imagine a network request here
return false;
}
And here it is in bytecode in MainActivity.smali:
# virtual methods
.method public checkLogin(Ljava/lang/String;Ljava/lang/String;)Z
.locals 1
.param p1, "username" # Ljava/lang/String;
.param p2, "password" # Ljava/lang/String;
.prologue
.line 43
const/4 v0, 0x0 //<-- This value is returned
return v0
.end method
The method checkLogin() returns the value of v0. We see in the line above, that v0 is set to 0x0 which means false. We want the method to return true so we edit 0x0 to 0x1 and save the file.
6) Build the apk
apktool b ReverseMe -o newReverseMev1.apk
Now we use Apktool to build the app again
7) Sign the apk
The last step is to sign the app.We need to create a keystore:
keytool -genkey -v -keystore my-release-key.keystore -alias myAlias -keyalg RSA -keysize 2048 -validity 10000
Then we use the keystore to sign the apk:
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore newReverseMev1.apk myAlias
We can now install the apk again and see that the “login” was successful.